Here,we are going to configure dynamic NAT with Pool of Public ip Address range by using packet
tracer.This type of Natting provides protection by hiding our real public ip address of our network.
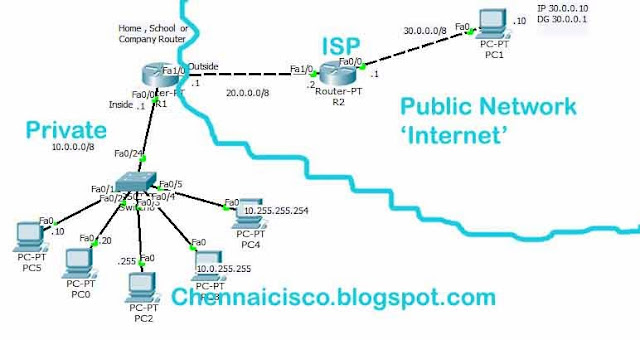
Step 1:Create topology like this,
Step 2:Configure ip address to all router interfaces and PC's
In Router R1,global config mode
R1(config)#interface fastethernet 0/0
R1(config-if)#ip address 10.0.0.1 255.0.0.0
R1(config-if)#no shutdown
R1(config-if)#exit
R1(config)#interface fastethernet 1/0
R1(config-if)#ip address 20.0.0.1 255.0.0.0
R1(config-if)#no shutdown
R1(config-if)#exit
In Router R2,global config mode
R2(config)#interface fastethernet 1/0
R2(config-if)#ip address 20.0.0.2 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#exit
R2(config)#interface fastethernet 0/0
R2(config-if)#ip address 30.0.0.1 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#exit
Step 3:Configure standard access list for the network 10.0.0.0
R1(config)#access-list 10 permit 10.0.0.0 0.255.255.255
Step 4:Choose interface for 'ip nat inside' and 'ip nat outside' command.Here, Interface fastethernet0/0 is inside and interface fastethernet1/0 is outside.
R1(config)#interface fastethernet0/0
R1(config-if)#ip nat inside
R1(config-if)#exit
R1(config)#interface fastethernet1/0
R1(config-if)#ip nat outside
R1(config-if)#exit
Step 5:Create a pool of address,I am going take range from 20.0.0.1 to 20.0.0.6.
R1(config)#ip nat pool publiciprange 20.0.0.1 20.0.0.6 netmask 255.255.255.248
Here,'publiciprange' name we give for this range of ip address.we can give what ever we want.Here our router pulic ip address is 20.0.0.1 and subnetmask 255.0.0.0.The range of ip address we are using is 20.0.0.1 20.0.0.6 with subnetmask 255.255.255.248.So, this ip address range is different than ip address in router interface.So person in public network can't see the real public ip of our network 20.0.0.1. They can only see the range of ip addres with differnet subnetmask this is also one type of security for our network.
Step 6:Configuring NAT with Pool 'publiciprange'.
R1(config)#ip nat inside source list 10 pool publiciprange
Step 7:configure static default route to forward all packets to any network to the next hop 20.0.0.2 or exit interface.
R1(config)#ip route 0.0.0.0 0.0.0.0 20.0.0.2
(or)
R1(config)#ip route 0.0.0.0 0.0.0.0 fastethernet1/0
Here,this both command do the same but distance metric is differnet for the first type is 1 for the Second 0.
Step 8:Now go router R1 and give this command in privileged mode,
R1#debug ip nat
By this command, we can see the translation process in router.
step 9:Click on PC->Desktop->command prompt->ping 30.0.0.10 and press 'enter'.Do this in all 5PC's immediately and check router R1 to seetranslation.i have got,
Translation in router R1,i will copy and paste some translations below
NAT: s=10.0.0.10->20.0.0.6, d=30.0.0.10 [9]
NAT*: s=30.0.0.10, d=20.0.0.6->10.0.0.10 [32]
NAT: s=10.0.0.10->20.0.0.6, d=30.0.0.10 [10]
NAT*: s=30.0.0.10, d=20.0.0.6->10.0.0.10 [33]
NAT: s=10.0.0.20->20.0.0.2, d=30.0.0.10 [9]
NAT: s=10.0.0.10->20.0.0.6, d=30.0.0.10 [11]
NAT*: s=30.0.0.10, d=20.0.0.6->10.0.0.10 [34]
NAT: s=10.0.0.255->20.0.0.3, d=30.0.0.10 [9]
NAT*: s=30.0.0.10, d=20.0.0.3->10.0.0.255 [35]
NAT: s=10.0.0.10->20.0.0.6, d=30.0.0.10 [12]
NAT*: s=30.0.0.10, d=20.0.0.6->10.0.0.10 [36]
NAT: s=10.0.0.255->20.0.0.3, d=30.0.0.10 [10]
Router will wait 30 seconds after that translations will be expired and ip address will be available again
NAT: expiring 20.0.0.6 (10.0.0.10) icmp 5 (5)
NAT: expiring 20.0.0.6 (10.0.0.10) icmp 6 (6)
NAT: expiring 20.0.0.2 (10.0.0.20) icmp 5 (5)
NAT: expiring 20.0.0.6 (10.0.0.10) icmp 7 (7)
NAT: expiring 20.0.0.6 (10.0.0.10) icmp 8 (8)
NAT: expiring 20.0.0.3 (10.0.0.255) icmp 5 (5)
NAT: expiring 20.0.0.3 (10.0.0.255) icmp 6 (6)
NAT: expiring 20.0.0.3 (10.0.0.255) icmp 7 (7)
NAT: expiring 20.0.0.4 (10.0.255.255) icmp 5 (5)
NAT: expiring 20.0.0.3 (10.0.0.255) icmp 8 (8)
NAT: expiring 20.0.0.4 (10.0.255.255) icmp 6 (6)
NAT: expiring 20.0.0.2 (10.0.0.20) icmp 6 (6)
NAT: expiring 20.0.0.4 (10.0.255.255) icmp 7 (7)
Troubleshooting commands,
R1#show ip nat translations
R1#show ip nat statistics
R1#clear ip nat translation *
R1#show running-config
R1#show ip route
tracer.This type of Natting provides protection by hiding our real public ip address of our network.
Step 1:Create topology like this,
Step 2:Configure ip address to all router interfaces and PC's
In Router R1,global config mode
R1(config)#interface fastethernet 0/0
R1(config-if)#ip address 10.0.0.1 255.0.0.0
R1(config-if)#no shutdown
R1(config-if)#exit
R1(config)#interface fastethernet 1/0
R1(config-if)#ip address 20.0.0.1 255.0.0.0
R1(config-if)#no shutdown
R1(config-if)#exit
In Router R2,global config mode
R2(config)#interface fastethernet 1/0
R2(config-if)#ip address 20.0.0.2 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#exit
R2(config)#interface fastethernet 0/0
R2(config-if)#ip address 30.0.0.1 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#exit
Step 3:Configure standard access list for the network 10.0.0.0
R1(config)#access-list 10 permit 10.0.0.0 0.255.255.255
Step 4:Choose interface for 'ip nat inside' and 'ip nat outside' command.Here, Interface fastethernet0/0 is inside and interface fastethernet1/0 is outside.
R1(config)#interface fastethernet0/0
R1(config-if)#ip nat inside
R1(config-if)#exit
R1(config)#interface fastethernet1/0
R1(config-if)#ip nat outside
R1(config-if)#exit
Step 5:Create a pool of address,I am going take range from 20.0.0.1 to 20.0.0.6.
R1(config)#ip nat pool publiciprange 20.0.0.1 20.0.0.6 netmask 255.255.255.248
Here,'publiciprange' name we give for this range of ip address.we can give what ever we want.Here our router pulic ip address is 20.0.0.1 and subnetmask 255.0.0.0.The range of ip address we are using is 20.0.0.1 20.0.0.6 with subnetmask 255.255.255.248.So, this ip address range is different than ip address in router interface.So person in public network can't see the real public ip of our network 20.0.0.1. They can only see the range of ip addres with differnet subnetmask this is also one type of security for our network.
Step 6:Configuring NAT with Pool 'publiciprange'.
R1(config)#ip nat inside source list 10 pool publiciprange
Step 7:configure static default route to forward all packets to any network to the next hop 20.0.0.2 or exit interface.
R1(config)#ip route 0.0.0.0 0.0.0.0 20.0.0.2
(or)
R1(config)#ip route 0.0.0.0 0.0.0.0 fastethernet1/0
Here,this both command do the same but distance metric is differnet for the first type is 1 for the Second 0.
Step 8:Now go router R1 and give this command in privileged mode,
R1#debug ip nat
By this command, we can see the translation process in router.
step 9:Click on PC->Desktop->command prompt->ping 30.0.0.10 and press 'enter'.Do this in all 5PC's immediately and check router R1 to seetranslation.i have got,
Translation in router R1,i will copy and paste some translations below
NAT: s=10.0.0.10->20.0.0.6, d=30.0.0.10 [9]
NAT*: s=30.0.0.10, d=20.0.0.6->10.0.0.10 [32]
NAT: s=10.0.0.10->20.0.0.6, d=30.0.0.10 [10]
NAT*: s=30.0.0.10, d=20.0.0.6->10.0.0.10 [33]
NAT: s=10.0.0.20->20.0.0.2, d=30.0.0.10 [9]
NAT: s=10.0.0.10->20.0.0.6, d=30.0.0.10 [11]
NAT*: s=30.0.0.10, d=20.0.0.6->10.0.0.10 [34]
NAT: s=10.0.0.255->20.0.0.3, d=30.0.0.10 [9]
NAT*: s=30.0.0.10, d=20.0.0.3->10.0.0.255 [35]
NAT: s=10.0.0.10->20.0.0.6, d=30.0.0.10 [12]
NAT*: s=30.0.0.10, d=20.0.0.6->10.0.0.10 [36]
NAT: s=10.0.0.255->20.0.0.3, d=30.0.0.10 [10]
Router will wait 30 seconds after that translations will be expired and ip address will be available again
NAT: expiring 20.0.0.6 (10.0.0.10) icmp 5 (5)
NAT: expiring 20.0.0.6 (10.0.0.10) icmp 6 (6)
NAT: expiring 20.0.0.2 (10.0.0.20) icmp 5 (5)
NAT: expiring 20.0.0.6 (10.0.0.10) icmp 7 (7)
NAT: expiring 20.0.0.6 (10.0.0.10) icmp 8 (8)
NAT: expiring 20.0.0.3 (10.0.0.255) icmp 5 (5)
NAT: expiring 20.0.0.3 (10.0.0.255) icmp 6 (6)
NAT: expiring 20.0.0.3 (10.0.0.255) icmp 7 (7)
NAT: expiring 20.0.0.4 (10.0.255.255) icmp 5 (5)
NAT: expiring 20.0.0.3 (10.0.0.255) icmp 8 (8)
NAT: expiring 20.0.0.4 (10.0.255.255) icmp 6 (6)
NAT: expiring 20.0.0.2 (10.0.0.20) icmp 6 (6)
NAT: expiring 20.0.0.4 (10.0.255.255) icmp 7 (7)
Troubleshooting commands,
R1#show ip nat translations
R1#show ip nat statistics
R1#clear ip nat translation *
R1#show running-config
R1#show ip route

The wildcard mask for the access-list is incorrect. It should be 0.255.255.255.
ReplyDeletesir access list wrong hi
ReplyDeletethe correct control access entry is R1(config)#access-list 10 permit 10.0.0.0 0.0.0.255
wildcard mask corrected,thank you to inform me slim red..
ReplyDeleteExactly what precisely are the use and conditions of your pool? Components like the consistency of usage alongside exactly how much junk falls into your pool may mean pretty much arrangements from your pool administration in a month. Schwimmbecken
ReplyDelete