How to Configure Same VLAN in Different Layer 2 Cisco Switches and Trunk Configuraion Using 802.1q
In this Post we are going to see how to configure VLAN in different Switches and we gonna check how it communicates with same VLAN on different Switches using Packet Tracer.
If a network has less number of host, that only needs single switch for the network.What if the network has larger number of host or Users.Host in a Same VLAN can communicate with each other if we configure host in same VLAN.Is it possible for the host to communicate from one switch to the host from other switch if the two host are in same VLAN.
Yes, VLAN can be extended to other switches in a network.we can make them commnicate with each other by connecting that two switches with cross cable and we have to configure that link as a Trunk.
Trunk and Access Links
Trunk Link
Trunk Links are the port that connects Switches and Routers.
Trunk Links are used to carry multiple VLAN frames across Switches in a network.
It makes VLANs to communicate with host in Same VLAN present in other switches.
Trunk Links can be configured between Switches and Routers with Cross cable as a Point to Point link.
It can be 100Mbps, 1gbps links.
Trunk links are the part of multiple VLAN's,So it uses ID created by frame tagging method.
Only Fastethernet ports can be trunk links.
Access Link
Acces links are the ports that connects end devices to Switches.
Access Link referred as native VLAN of the port.
Access Links are unaware of VLAN Information, Switches strips VLAN information before it sends of out through access link.
Hosts connected to access link doesn't know about the VLAN ID.
This links are belongs to only one VLAN.
Frame Tagging
By using this we can create a VLANs that can be forwarded across switches in a network.
VLAN ID will be added once the frames reaches the switch.End devices unaware of VLAN in a network.
End devices creates and sends data without any VLAN information, Only switch adds VLAN information by frame tagging and it sends to switches in network.
Once that frame reaches the switch, it first job is to identify VLAN ID
If theres is a same VLAN that sender belongs to,the switch will send out through only that port.If same VLAN not present then,Switch will drop the frames.
Frame Tagging Methods
There are two types of frame tagging methods
Inter Switch Link-ISL
IEEE802.1q
Inter Switch Links is proprietary to Cisco switches.
ISL is used for fastEthernet links and Gigabit Ethernet links only.
We cannot use this in diffrent vendor switches,we can only use in cisco switches.
ISL is performed with ASIC(Application Specific Integrated Circuits)
Efficient between cisco switche to switch,Router to Switch.
Steps to Configure VLAN in different Switches and how it communicates with each other with trunk link.
Step 1: Create a topology with two switches and connect PC's like in a below topology.
Note:- Here all VLAN host were configured with IP in Same network to make you understand VLAN in better way. In realtime, we have to use different network for each VLAN to achieve Inter VLAN routing. It can be classful network or subnetted network based on our requirement.
In above topology in left switch there are two VLAN configured one is VLAN 2 name Red,another one is VLAN 3 name Blue.In Right switch configured with VLAN 4 name Green and VLAN 3 name Blue.
Step 2:Configure switch with VLAN and assign IP address to all host with IP address.Link to How to configure IP address to PC
Before configuring VLAN Ping IP 10.0.0.50,10.0.0.20,10.0.0.100 from 10.0.0.40
Click on PC3->Desktop->Command Prompt then give this command and check
Ping 10.0.0.50
PIng 10.0.0.20
Ping 10.0.0.100
Above result shows we can get reply from all host without vlan configuration,From other switches..
Now, We are going to see how to create VLAN in Cisco Switch.For that go to global configuration mode and do this configuration to create VLANs.
In Left Switch,
Switch(config)#
Switch(config)#vlan 2
Switch(config-vlan)#name red
Switch(config-vlan)#exit
Switch(config)#vlan 3
Switch(config-vlan)#name blue
Switch(config-vlan)#exit
In Right Switch
Switch(config)#vlan 3
Switch(config-vlan)#name blue
Switch(config-vlan)#exit
Switch(config)#vlan 4
Switch(config-vlan)#name green
Switch(config-vlan)#exit
After creating VLAN assign ports to appropriate interafaces.Enter this command in global configuration mode in switches.
Left Switch (Interface Fastethernet0/1-3 adding to VLAN 2
Switch(config)#interface range fastethernet0/1-3
Switch(config-if-range)#switchport mode access
Switch(config-if-range)#switchport access vlan 2
Switch(config-if-range)#exit
Left switch (Interface Fastethernet0/4-6) configured to VLAN 3
Switch(config)#
Switch(config)#interface range fastethernet0/4-6
Switch(config-if-range)#switchport mode access
Switch(config-if-range)#switchport access vlan 3
Switch(config-if-range)#exit
Right Switch (Interface Fastethernet0/1& 0/2) configured to VLAN 4
Switch(config)#interface range fastethernet0/1-2
Switch(config-if-range)#switchport mode access
Switch(config-if-range)#switchport access vlan 3
Switch(config-if-range)#exit
In Right Switch (Interface Fastethernet0/3& 0/4 Configured to VLAN 3
Switch(config)#interface range fastethernet0/3-4
Switch(config-if-range)#switchport mode access
Switch(config-if-range)#switchport access vlan 3
Switch(config-if-range)#exit
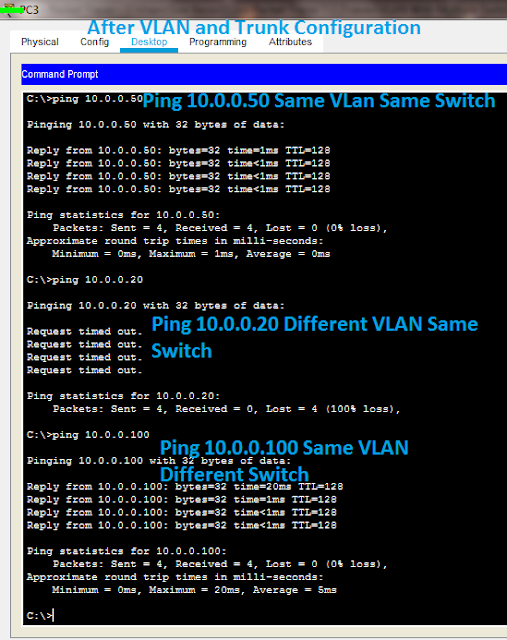
After VLAN configuration Ping same IPs that was pinged before without VLAN.Below image shows the ping result after VLAN configuration.By default host not configured with any VLAN will be assingned to VLAN1.VLAN1 is called as native VLAN
In above image shows pinging IP 10.0.0.100 failed even it is belongs to VLAN 3.Because,the link that connects this two switch must be configured as trunk.
Switch cannont forward over access link,so we have to configure link fastethernet0/23 of left switch and fastethernet0/23 of right switch as trunk.CLI command to configure interface fastethernet as trunk is given below.
In Left Switch,
Switch#
Switch#config t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#
Switch(config)#interface fastethernet0/23
Switch(config-if)#switchport mode trunk
Switch(config-if)#exit
In Right Switch,
Switch#
Switch#%SPANTREE-2-RECV_PVID_ERR: Received 802.1Q BPDU on non trunk FastEthernet0/23 VLAN1.
%SPANTREE-2-BLOCK_PVID_LOCAL: Blocking FastEthernet0/23 on VLAN0001. Inconsistent port type.
we will get above message once we configured VLAN on one side of the link.VLAN configured in Left Switch,we got this message in the right switch.
Switch#
Switch#config t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#
Switch(config)#interface fastethernet0/23
Switch(config-if)#switchport mode trunk
Switch(config-if)#exit
Once, We configured the interface as trunk, host in one switch can communicate with host in other switch, If it is in same VLAN.No need to configure Encapsulation 802.1q Layer 2 Cisco Switch.
Ping result shows, host 10.0.0.40and 10.0.0.100 can communicate with 10.0.0.50 in a same vlan even host in different switch after trunk configuration, 10.0.0.20 failed because it is in different VLAN
To check VLAN configuration,enter this command in privileged mode.
Switch#
Switch#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/7, Fa0/8, Fa0/9, Fa0/10
Fa0/11, Fa0/12, Fa0/13, Fa0/14
Fa0/15, Fa0/16, Fa0/17, Fa0/18
Fa0/19, Fa0/20, Fa0/21, Fa0/22
Fa0/24
2 red active Fa0/1, Fa0/2, Fa0/3
3 blue active Fa0/4, Fa0/5, Fa0/6
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
To check Trunk configuration details,enter this command in privileged mode,
Switch#show interface trunk
Port Mode Encapsulation Status Native vlan
Fa0/23 on 802.1q trunking 1
Port Vlans allowed on trunk
Fa0/23 1-1005
Port Vlans allowed and active in management domain
Fa0/23 1,2,3
Port Vlans in spanning tree forwarding state and not pruned
Fa0/23 1,2,3
You may interested in,
How to configure VLAN in single switch using Packet Tracer
Inter-VLAN Routing in Packet Tracer



Post a Comment